Securely Connect Remote IoT VPC On AWS: A Comprehensive Guide
Connecting remote IoT devices to a Virtual Private Cloud (VPC) on AWS securely is critical for modern businesses leveraging IoT technology. With the increasing number of IoT devices deployed globally, ensuring secure communication and data transfer has become more important than ever. AWS provides robust tools and services to create a secure environment for IoT devices, making it easier for organizations to manage and protect their IoT ecosystems.
In today's digital landscape, IoT devices are transforming industries by enabling real-time data collection and analysis. However, these devices often operate in remote locations, making it essential to establish secure connections with cloud infrastructure. AWS offers cutting-edge solutions to address these challenges, ensuring data integrity and security at every stage of the IoT lifecycle.
This article delves into the intricacies of securely connecting remote IoT devices to a VPC on AWS. By exploring best practices, tools, and configurations, we aim to provide actionable insights for IT professionals and decision-makers looking to enhance their IoT security posture. Let's explore how AWS can help you achieve this goal effectively.
Read also:Wirral Pregnancy Photographer Capturing The Beauty Of Motherhood
Table of Contents
- Overview of Securely Connecting IoT Devices on AWS
- Understanding VPC Basics for IoT Deployment
- AWS IoT Services for Secure Connections
- Security Best Practices for IoT on AWS
- Designing a Secure Network Architecture for IoT
- Implementing Encryption for IoT Data
- Authentication and Authorization for IoT Devices
- Monitoring and Logging IoT Activities
- Real-World Case Studies of Secure IoT Deployments
- Future Trends in IoT Security on AWS
Overview of Securely Connecting IoT Devices on AWS
As organizations adopt IoT technologies, the need for secure connectivity becomes paramount. AWS provides a comprehensive suite of tools and services to ensure that remote IoT devices can communicate with cloud infrastructure safely and efficiently. By leveraging AWS's Virtual Private Cloud (VPC), businesses can create isolated environments for their IoT devices, reducing the risk of unauthorized access and data breaches.
Key Features of AWS IoT Solutions:
- Scalable infrastructure to handle millions of IoT devices
- Advanced security features for data encryption and authentication
- Integration with other AWS services for seamless operations
- Customizable configurations to meet specific business needs
Understanding the fundamentals of AWS IoT services is crucial for implementing secure connections. This section will explore how AWS VPC can be utilized to create a secure environment for IoT devices.
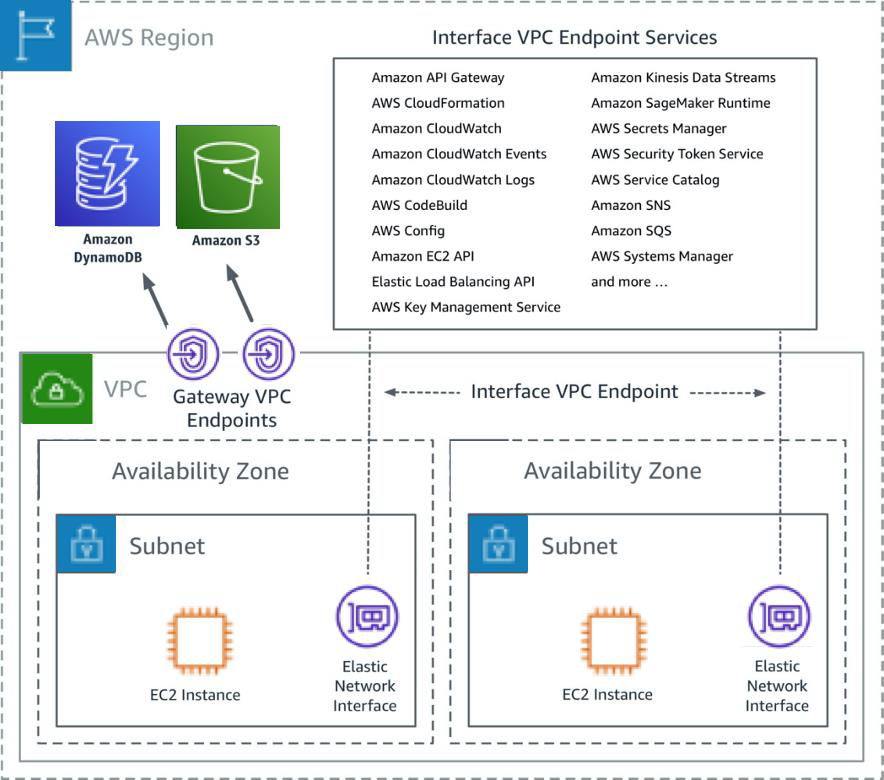
Understanding VPC Basics for IoT Deployment
What is a VPC?
A Virtual Private Cloud (VPC) on AWS is a logically isolated section of the AWS Cloud where you can launch AWS resources in a virtual network that you define. This isolation ensures that your IoT devices and applications operate in a secure environment, protected from external threats.
Key Components of a VPC
When deploying IoT devices on AWS, it's important to understand the key components of a VPC:
- Subnets: Divides your VPC into smaller segments for better organization and security.
- Internet Gateways: Enables communication between your VPC and the internet.
- Security Groups: Acts as a virtual firewall for your instances, controlling inbound and outbound traffic.
- Network Access Control Lists (NACLs): Provides an additional layer of security by controlling traffic at the subnet level.
By configuring these components correctly, you can ensure that your IoT devices are securely connected to your VPC on AWS.
Read also:The Inspiring Story Of E40 The Legendary Bay Area Rapper And Entrepreneur
AWS IoT Services for Secure Connections
AWS offers a range of IoT services designed to facilitate secure connections between remote devices and cloud infrastructure. These services include:
- AWS IoT Core: A managed cloud service that allows connected devices to securely interact with cloud applications and other devices.
- AWS IoT Device Defender: Monitors device behavior and detects anomalies that could indicate security issues.
- AWS IoT Device Management: Provides tools for onboarding, organizing, monitoring, and remotely managing IoT devices at scale.
These services work together to create a secure and scalable environment for IoT devices, ensuring that data is transmitted safely and efficiently.
Security Best Practices for IoT on AWS
1. Use Strong Authentication Mechanisms
Implementing strong authentication mechanisms is essential for securing IoT devices. AWS IoT Core supports X.509 certificates and AWS IoT Device Defender provides tools for monitoring device behavior and detecting anomalies.
2. Enable Encryption for Data in Transit and at Rest
Encrypting data ensures that sensitive information remains protected both during transmission and when stored in the cloud. AWS provides tools such as AWS Key Management Service (KMS) and AWS CloudHSM to manage encryption keys securely.
3. Regularly Update and Patch Devices
Keeping IoT devices up to date with the latest security patches is crucial for maintaining a secure environment. AWS IoT Device Management simplifies this process by providing tools for remote updates and monitoring.
Designing a Secure Network Architecture for IoT
Designing a secure network architecture involves several key considerations:
- Segmentation: Divide your VPC into subnets to isolate different types of devices and applications.
- Access Control: Use security groups and NACLs to control access to your IoT devices and applications.
- Monitoring: Implement monitoring and logging tools to detect and respond to security incidents quickly.
By following these guidelines, you can create a robust network architecture that protects your IoT devices and data from potential threats.
Implementing Encryption for IoT Data
Why Encryption Matters
Encryption plays a vital role in securing IoT data by converting sensitive information into a format that cannot be easily read by unauthorized parties. AWS provides several tools for implementing encryption, including:
- AWS KMS: A managed service that makes it easy to create and control encryption keys.
- AWS CloudHSM: A hardware security module that helps meet corporate, contractual, and regulatory compliance requirements for data security.
By leveraging these tools, organizations can ensure that their IoT data remains secure both in transit and at rest.
Authentication and Authorization for IoT Devices
Authentication and authorization are critical components of IoT security. AWS IoT Core provides robust tools for managing device authentication and authorization, including:
- X.509 Certificates: A widely used standard for digital certificates that verifies the identity of devices.
- Custom Authorizers: Allows you to define custom authentication mechanisms using Lambda functions.
By implementing these mechanisms, organizations can ensure that only authorized devices can access their IoT ecosystem.
Monitoring and Logging IoT Activities
Why Monitoring is Important
Monitoring and logging IoT activities is essential for detecting and responding to security incidents quickly. AWS provides several tools for monitoring IoT devices, including:
- AWS CloudWatch: A monitoring service that provides insights into application and system health.
- AWS IoT Device Defender: Monitors device behavior and detects anomalies that could indicate security issues.
By leveraging these tools, organizations can gain visibility into their IoT ecosystem and respond to potential threats in real time.
Real-World Case Studies of Secure IoT Deployments
Several organizations have successfully implemented secure IoT deployments on AWS. For example:
- Company A: A manufacturing company used AWS IoT Core to securely connect thousands of IoT devices to its cloud infrastructure, improving operational efficiency and reducing downtime.
- Company B: A healthcare provider implemented AWS IoT Device Defender to monitor medical devices, ensuring patient data remained secure and compliant with regulatory requirements.
These case studies demonstrate the effectiveness of AWS IoT services in securing IoT deployments across various industries.
Future Trends in IoT Security on AWS
The future of IoT security on AWS is promising, with several trends emerging:
- Machine Learning for Threat Detection: AWS is investing in machine learning technologies to enhance threat detection and response capabilities.
- Edge Computing: As IoT devices become more powerful, edge computing will play a crucial role in processing data closer to the source, reducing latency and improving security.
- Quantum-Safe Cryptography: With the advent of quantum computing, AWS is exploring quantum-safe cryptography to ensure long-term data security.
By staying informed about these trends, organizations can prepare for the future of IoT security and continue to protect their ecosystems effectively.
Conclusion
In conclusion, securely connecting remote IoT devices to a VPC on AWS requires a comprehensive approach that addresses key aspects of security, including authentication, encryption, monitoring, and network architecture. By leveraging AWS IoT services and following best practices, organizations can create a secure and scalable environment for their IoT devices.
We invite you to share your thoughts and experiences in the comments section below. Additionally, feel free to explore other articles on our site for more insights into IoT security and AWS solutions. Together, let's build a safer and more connected world.
Article Recommendations