Securely Connect Remote IoT VPC On AWS: A Comprehensive Guide
As the Internet of Things (IoT) continues to expand, securely connecting remote IoT devices within a Virtual Private Cloud (VPC) on AWS has become a critical requirement for businesses. Organizations are increasingly relying on AWS to create robust and secure infrastructures that can handle the demands of IoT ecosystems. However, ensuring that these connections remain secure while maintaining high performance is no small feat.
With billions of IoT devices now connected globally, securing data transmissions and ensuring privacy has become paramount. AWS provides a wide range of tools and services designed to help businesses achieve this goal, from VPC configurations to advanced encryption methods. This article will delve into the best practices for securely connecting remote IoT devices within an AWS VPC environment.
Whether you're a network administrator, DevOps engineer, or IT professional, understanding how to configure and secure IoT devices on AWS is essential. This guide will provide actionable insights, practical tips, and expert recommendations to help you build a secure and scalable IoT infrastructure.
Read also:Mr Krabs Pumpkin A Comprehensive Guide To The Iconic Spongebob Squarepants Episode
Table of Contents
- Introduction to AWS VPC
- IoT Security Challenges
- Why Use AWS for IoT?
Setting Up AWS VPC for IoT
- Securing Remote IoT Connections
- Network Security Best Practices
- Data Protection and Encryption
- Monitoring and Logging
- Cost Optimization
- Future Trends in IoT Security
Introduction to AWS VPC
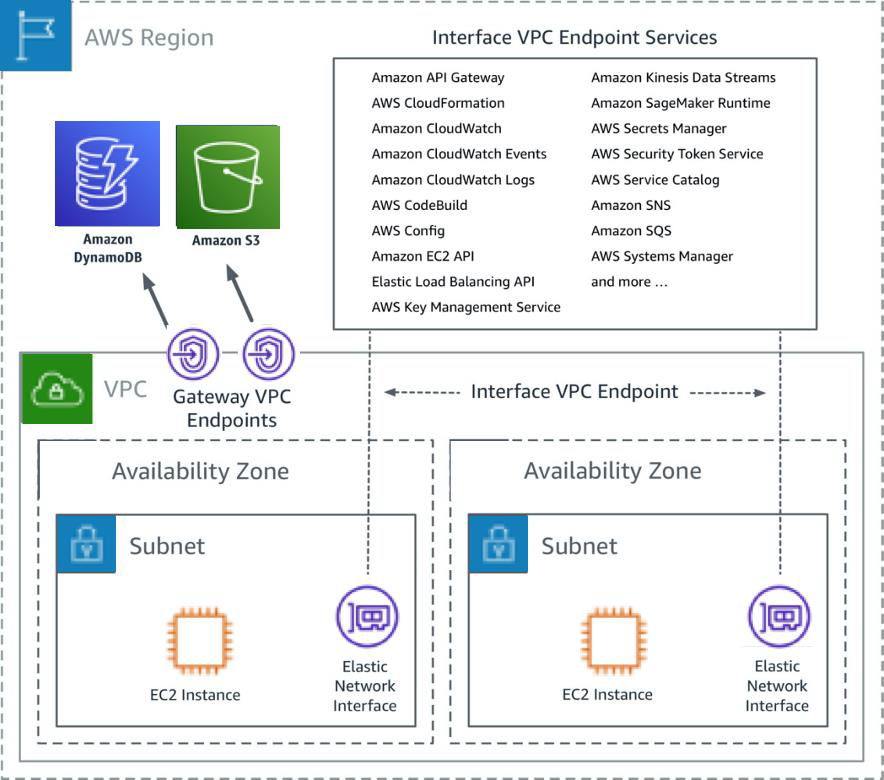
AWS Virtual Private Cloud (VPC) is a foundational service that allows users to create an isolated network environment within the AWS cloud. It provides a secure and scalable infrastructure for deploying applications, databases, and IoT devices. By leveraging VPC, organizations can define their own IP address ranges, create subnets, and configure route tables to control traffic flow.
For IoT deployments, AWS VPC plays a crucial role in ensuring secure communication between devices and the cloud. It enables the creation of private subnets for sensitive data, while public subnets can be used for internet-facing services. This separation enhances security and helps protect IoT devices from unauthorized access.
IoT Security Challenges
The rapid growth of IoT devices has introduced several security challenges that organizations must address. One of the primary concerns is the potential for unauthorized access to devices and data. Without proper security measures, IoT devices can become entry points for cyberattacks, leading to data breaches and financial losses.
Key Challenges Include:
- Device Authentication: Ensuring that only authorized devices can connect to the network.
- Data Encryption: Protecting data in transit and at rest from interception and tampering.
- Network Segmentation: Isolating IoT devices from other network resources to minimize risks.
- Regular Updates: Keeping firmware and software up to date to patch vulnerabilities.
Why Use AWS for IoT?
AWS offers a comprehensive suite of services tailored for IoT deployments, making it an ideal choice for organizations looking to securely connect remote IoT devices. AWS IoT Core, for example, provides a managed service that allows billions of devices to connect and interact with cloud applications and other devices securely.
In addition to IoT Core, AWS offers services like AWS IoT Device Defender, which helps monitor and audit device behavior to detect anomalies, and AWS IoT Greengrass, which enables local compute, messaging, and data caching for connected devices. These services work together to create a robust and secure IoT ecosystem.
Setting Up AWS VPC for IoT
Configuring AWS VPC for IoT involves several steps to ensure a secure and efficient setup. Below is a step-by-step guide:
Read also:Brandi Belle A Comprehensive Guide To Her Career And Influence In The Adult Entertainment Industry
Step 1: Create a VPC
Start by creating a new VPC in the AWS Management Console. Define the IP address range and choose the appropriate region for your deployment.
Step 2: Configure Subnets
Divide your VPC into public and private subnets. Public subnets can be used for internet-facing services, while private subnets are ideal for securing IoT devices.
Step 3: Set Up Security Groups
Create security groups to control inbound and outbound traffic for your IoT devices. Use rules to allow only necessary ports and protocols.
Securing Remote IoT Connections
Securing remote IoT connections is essential to protect sensitive data and prevent unauthorized access. AWS provides several tools and best practices to achieve this:
Use TLS Encryption
Transport Layer Security (TLS) is a protocol that ensures secure communication between IoT devices and the cloud. AWS IoT Core supports TLS 1.2, providing strong encryption for data in transit.
Implement Device Authentication
Device authentication ensures that only authorized devices can connect to your AWS VPC. AWS IoT Core supports X.509 certificates and custom authentication methods to verify device identity.
Network Security Best Practices
Implementing network security best practices is crucial for maintaining a secure IoT environment. Below are some recommendations:
- Use Network Access Control Lists (NACLs) to filter traffic at the subnet level.
- Regularly review and update security group rules to reflect current needs.
- Enable VPC Flow Logs to monitor and analyze traffic patterns.
Data Protection and Encryption
Data protection is a critical aspect of IoT security. AWS provides various encryption options to safeguard data both in transit and at rest:
In Transit Encryption
Use AWS Certificate Manager (ACM) to obtain and manage SSL/TLS certificates for encrypting data in transit. This ensures that data remains secure as it travels between devices and the cloud.
At Rest Encryption
Leverage AWS Key Management Service (KMS) to manage encryption keys and encrypt data stored in Amazon S3 or Amazon RDS.
Monitoring and Logging
Monitoring and logging are essential for detecting and responding to security incidents. AWS provides several tools for this purpose:
AWS CloudTrail
CloudTrail captures API activity in your AWS account, providing a detailed audit trail of all actions taken. This helps identify unauthorized access or suspicious activity.
AWS CloudWatch
CloudWatch allows you to monitor metrics and set alarms for critical events. Use it to track resource usage and detect anomalies in your IoT environment.
Cost Optimization
While security is a top priority, cost optimization is also important for IoT deployments. AWS offers various tools and strategies to help manage costs effectively:
Use Reserved Instances
Reserved Instances provide significant savings compared to On-Demand pricing for long-term workloads. Consider using them for stable IoT workloads.
Enable Auto Scaling
Auto Scaling ensures that resources are dynamically adjusted based on demand, preventing over-provisioning and reducing costs.
Future Trends in IoT Security
The future of IoT security is shaped by emerging technologies and evolving threats. Some key trends to watch include:
- Artificial Intelligence (AI) and Machine Learning (ML): These technologies are being used to detect and respond to security threats in real-time.
- Zero Trust Architecture: A security model that assumes no implicit trust, requiring continuous verification of devices and users.
- Quantum Computing: While still in its infancy, quantum computing has the potential to break traditional encryption methods, prompting the development of quantum-resistant algorithms.
Conclusion
Securing remote IoT devices within an AWS VPC environment requires a combination of best practices, advanced tools, and a proactive approach to threat management. By leveraging AWS services like IoT Core, VPC, and CloudTrail, organizations can create a secure and scalable IoT infrastructure that meets the demands of today's connected world.
We encourage readers to implement the strategies outlined in this article and stay informed about the latest trends in IoT security. For further reading, explore additional resources on AWS and IoT security. Don't forget to leave a comment or share this article with your network!
Article Recommendations